Wireless Threat Intelligence
Securing the modern, wireless world
The Threat
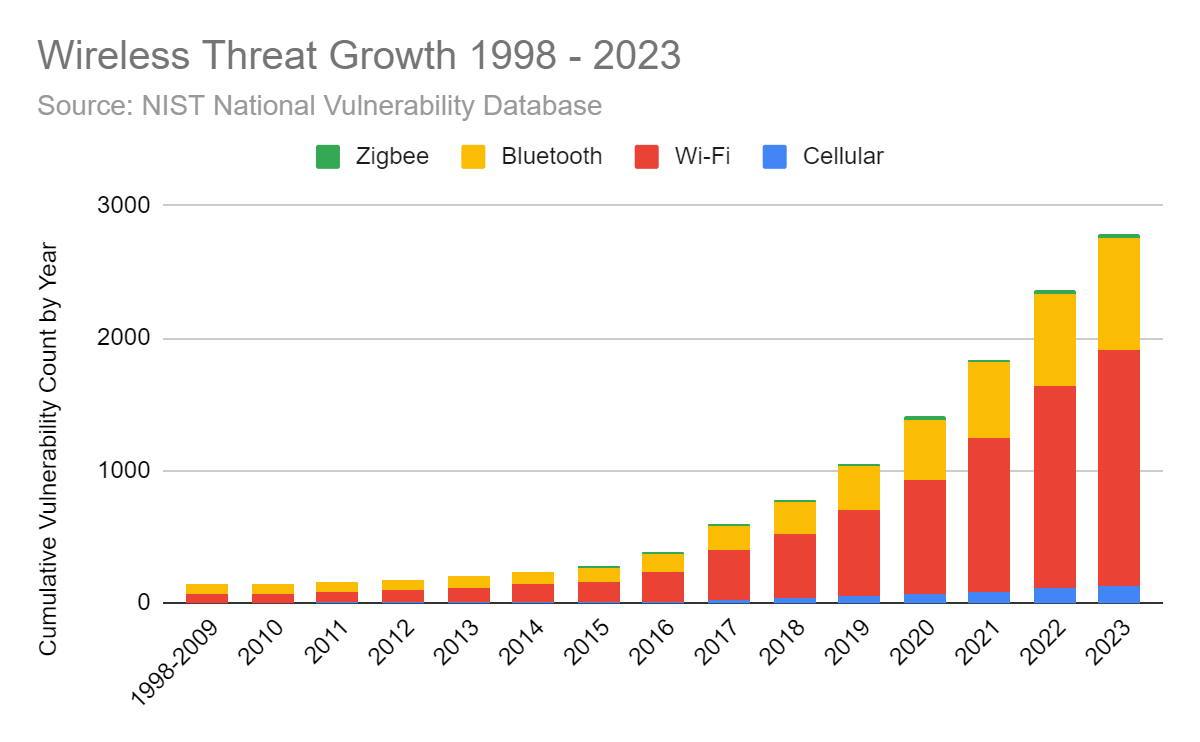
An explosion of wireless vulnerabilities in recent years has created a weakness in the security posture of many organizations. With nearly 3000 CVEs published based on wireless protocols, the wireless attack surface is highly vulnerable to exploitation and largely ignored by most security solutions.
Wireless protocols use Radio Frequencies (RF) to transmit information. Similar to sunlight, those waves travel at the speed of light, but unlike sunlight, they penetrate physical barriers and are invisible to the eye. A basic tenet of security is you can’t protect what you can’t see.
The Solution
Bastille provides the tools to secure the invisible wireless attack surface. With its patented solution of broadband, multi-channel RF sensors, highly scalable architecture, and advanced analytics, Bastille detects, locates, and adjudicates wireless signals.
Bastille collects a comprehensive set of data about every wireless device including their location over time, manufacturer, and transmission activities and overall behavior.
Bastille automatically identifies aberrant or malicious behavior and integrates with third-party systems to provide alerts and execute automated responses. Bastille’s advanced analytics engine, fueled with machine learning algorithms and backed by 30+ patents, provides insights into both known wireless infrastructure and other detected wireless devices using spatial, temporal, and behavioral information. The result is the world’s first Wireless Threat Intelligence Platform.
Wireless Threat Intelligence = Wireless Detection + Advanced Analytics
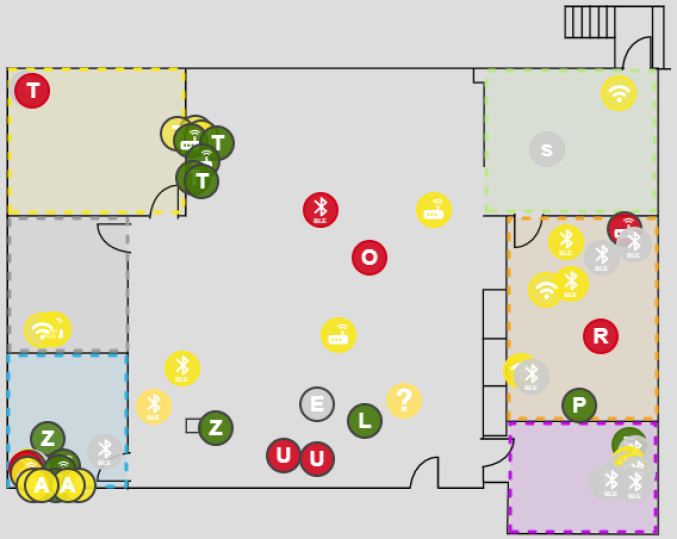
Bastille displays each device as an icon on a floor plan whose color indicates the threat level assigned by the threat intelligence platform.
Use Cases
Bastille is deployed among some of the world’s largest commercial companies and government agencies. Common use cases include cloud infrastructure wireless security, wireless intrusion detection (WIDS), classified area protection, C-suite protection, manufacturing, and others.
Enterprise
Cloud infrastructure wireless security
C-suite protection
Secure storage/computing facilities
Manufacturing (CPS / OT)
Trading floors
Call centers
Government
Wireless security for classified areas
Wireless intrusion detection system (WIDS) requirements
In-place monitoring systems
Forward-deployed wireless audits
General
Cellular intrusion detection
Continuous TSCM
Portable use cases
The Bastille System
DETECTION AND RESPONSE
Bastille Sensor Array
Wireless monitoring is enabled by Bastille’s sensor arrays, which detect wireless activity from 25 MHz to 6 GHz including cellular, Wi-Fi, Bluetooth, Bluetooth Low Energy, Zigbee, and other 802.15.4 / IoT protocols. The sensor arrays are 100% passive (they never transmit), are plenum rated, and are available for both indoor and IP67 ruggedized outdoor use.
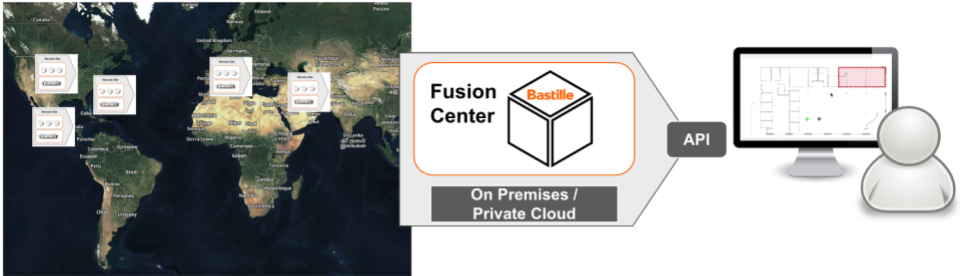
Bastille’s Fusion Center receives wireless data from the sensor arrays, compiles and analyzes the data, and serves web-based user interfaces to display current and historical wireless activity.
The Fusion Center implements the threat analysis engine to detect wireless threats and provides reporting functions and integrations with SIEM/SOAR, MDM/UDM, incident response, and other physical and network security systems.
Bastille’s architecture is API-first and globally scalable to meet the most demanding Enterprise Security needs